August 12, 2023

Calculation the Cost of Downtime
The cost of downtime can vary greatly from business to business but generally the more revenue the company brings in each year the higher the cost of each minute of downtime. There are many factors to account for when calculating this cost: lost revenue during the downtime, cost of employee productivity, lost revenue because of any lost customers, and even projected losses from damaged reputation. This does not include the costs of reactively fixing the technology itself. All these costs can be reduced when technology is maintained on a regular basis.
Calculating the Cost of Downtime
In the possibly disastrous event of software errors, hardware failure, or cyberattack, even minutes of downtime could result in revenue loss. The calculations below can be used to determine the loss accrued with examples listed at the end.
Formulas:
t = Number of minutes of downtime in all formulas
Revenue Lost
In the example of a business operating 8 hours a day/5 days a week, dividing the number of yearly sales or income by 124,800 (minutes in a year) you can find the revenue lost per minute.
Cost of Lowered Employee Productivity
Employee labor cost is also a factor when calculating loss if the employee(s) affected are still on the clock. This can be mitigated for hourly employees if they can be sent home early.
W = Hourly wage per employee
E_affected = Number of affected employees
Cost of IT Recovery
The cost of IT services to get systems up and running again should be calculated as well. However this cost can also be mitigated depending on the managed services plan and backup systems in place to cut down on billable time.
E_IT = Number of employees engaged IT recovery
t’ = Time to get operations running normally
![]()
Projected Lost Revenue from Lost Customer Loyalty
The revenue loss from loyal customers should be considered if applicable. Downtime that does not result in project delays or missed deadlines will not result in much, if any, revenue loss.
R_loss = Revenue lost during downtime
r = Average rate of repeat sales
Projected Loss of Revenue from Damage to Reputation
The loss from referrals and reputation can also be calculated. If there is no impact on customers there will be minimal revenue lost.
r’ = Percentage of sales referred by other clients
The total revenue lost can be determined by adding the results of all previous calculations.
Real World Examples
These examples do not include lost loyalty or damage to reputation as those are not always applicable.
Example 1:
$500,000 a year in revenue, 15 employees making $25 an hour.
R_loss = ($500,000/124,800) x 60 = $240.38/hour
C_prod = $25 x 15 x 1 = $375/hour
C_rec = $25 x 1 x 1 = $25/hour
TCoDT = $240.38 + $375.00 + $25.00 = $640.38
The total cost of each hour of downtime is $765.38.
Example 2:
$1,000,000 a year in revenue, 35 employees making $25 an hour.
R_loss = ($100,000/124,800) x 60 = $480.77/hour
C_prod = $25 x 35 x 1 = $875/hour
C_rec = $25 x 1 x 1 = $25/hour
TCoDT = $480.77 + $875.00 + $25.00 = $1380.77
The total cost of each hour of downtime is $1380.77.
If you would like to use an online calculator to estimate potential losses, Datto provides one here: https://www.datto.com/rto/
There are sometimes instances of complete data loss that can cost up to $50,000 or $100,000 for a company. Losses can also occur due to more minor technology issue that happen frequently. For example, an employee accidentally deletes a file and has to rebuild it from scratch. There may be individual time wasted due to poor PC performance. These events are likely not going to break a business but are going to add up in terms of time wasted and overall cost to a company.
The We Care Way to Reduce Downtime
1. Regular Server and Network Maintenance
Our Server Support plans help ensure that your server and networking devices are routinely kept up to date. A server is the heart of a technological infrastructure and often houses information that companies REQUIRE to operate. If this important piece of hardware should fail it can cost exponentially more to recover this data or rebuild the system if proper preventative measures are not taken. Our staff will monitor backups, check event logs, perform necessary security patches, and make sure your networking equipment is communicating the way it should be.
2. User Support and Maintenance
Many times, employees will work around an issue instead of reporting it for resolution. Seemingly trivial items can lead to inefficient practices in day-to-day operations that add up to large amounts of lost productivity and can cost a business big money. With user support, your staff will be able to submit tickets directly to our staff for quick review and troubleshooting, ask any questions that may be in the back of their mind, and get back to working at full capacity knowing we are on the case.
In addition, signing up for a User Support agreement allows us to dedicate the resources needed to get any issues resolved in an even more expedited manner. If your business comes to a grinding halt, you should expect your IT providers to begin support in a timely fashion. The unlimited remote support hours included in the maintenance agreement can be used for review or full resolution of IT needs during our regular business hours to meet the need for quick and quality service.
If you are interested in discussing User Support and preventing potential financial losses in your company, please contact us at info@wecarecomputers.com.
May 12, 2023

Why Choose Egnyte Cloud File Management?
Egnyte cloud-based file management and sharing platform offers several features that differentiate it from Microsoft OneDrive and SharePoint. Some of these features include:
- Hybrid deployment: Egnyte offers a hybrid deployment model that allows users to store some data in the cloud and other data on-premises. This provides more flexibility and control for businesses that may have regulatory or compliance requirements.
- Customizable user interface: Egnyte allows users to customize their user interface to meet their specific needs, making it easier to navigate and find the files they need quickly.
- Robust security: Egnyte provides enterprise-level security features such as data encryption, multi-factor authentication, and granular access controls. This makes it a more secure option for businesses that deal with sensitive data.
- Collaboration tools: Egnyte provides a range of collaboration tools that make it easy for teams to work together on projects, including real-time co-authoring, commenting, and version control.
- Scalability: Egnyte can scale to support businesses of all sizes, from small startups to large enterprises, making it a more versatile option than OneDrive or SharePoint.
- Comprehensive integration options: Egnyte integrates with a wide range of third-party applications, including Microsoft Office, Salesforce, and Google Workspace, making it easier to work with the tools you already use.
- Overall, Egnyte provides a more comprehensive and flexible solution for businesses that need to manage and share files securely, collaborate effectively, and scale to meet their changing needs.
If you are interested in setting up Egnyte for your company contact us at info@wecarecomputers.com.
May 11, 2023

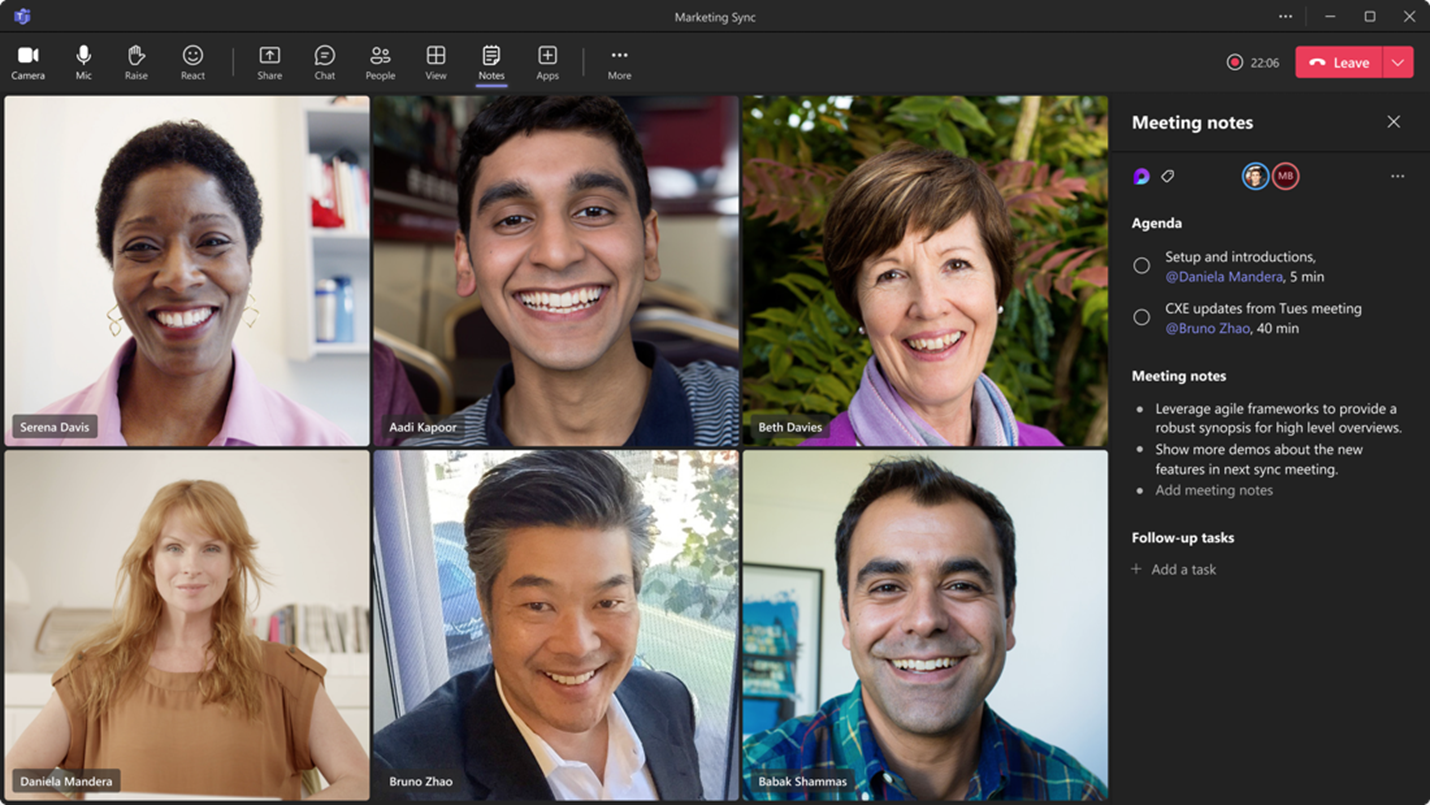
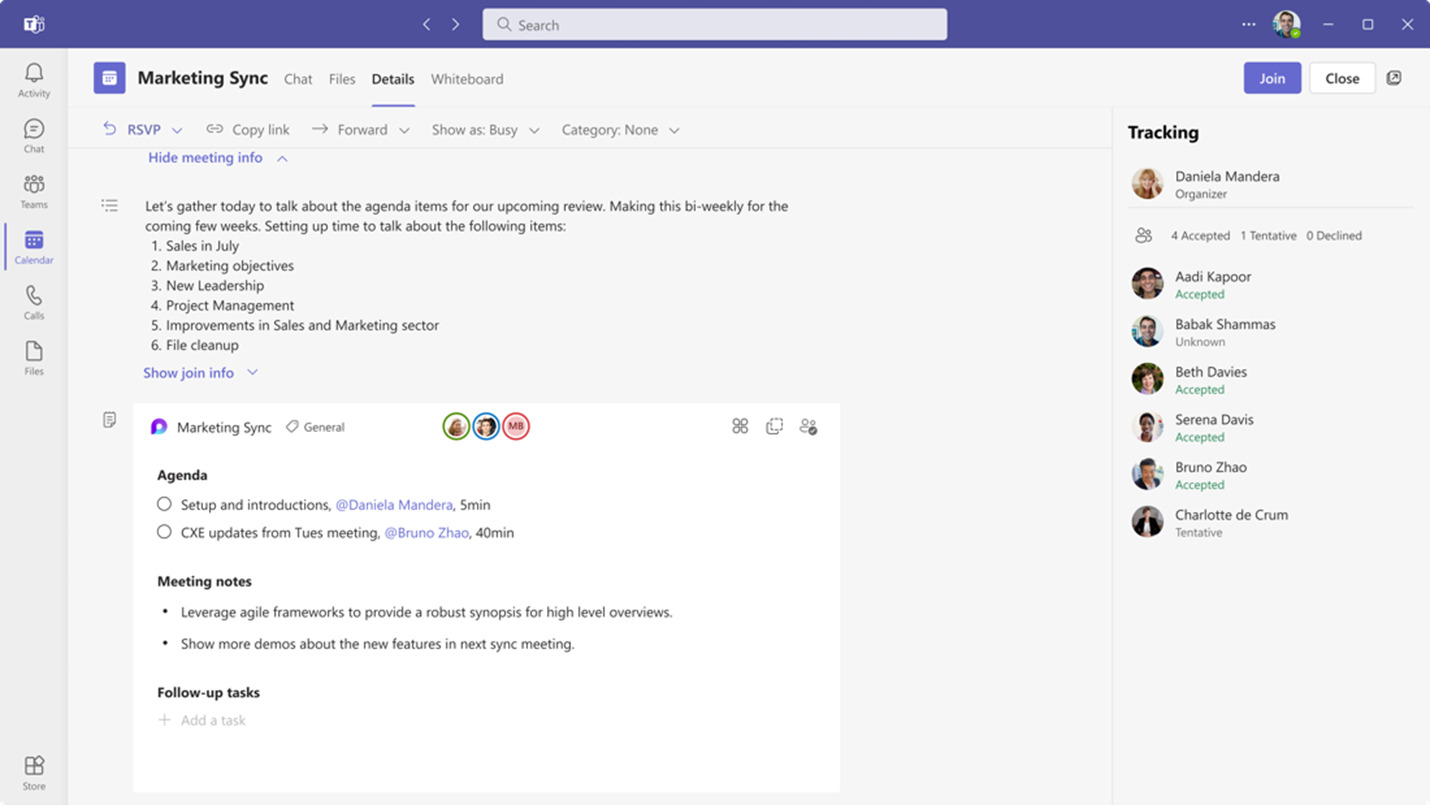
Collaborative Notes announced for Teams
Collaborative notes allow meeting attendees to co-create and collaborate on their meeting agenda, notes, and action items. The capability to track discussion items (Agenda), decisions (Notes) and follow-up items (Follow-up Tasks) is now integrated into the end-to-end meeting experience in Teams, Loop, Planner, To Do, Office.com and OneDrive for Business. These notetaking features come as a welcome addition to Teams preventing the need for separate OneNote meeting minutes or other notetaking software.
Users within the meeting will see a Notes button to initiate the new capabilities. The meeting notes will be shown on the right pane of the meeting window with the ability to open them in the browser for more room or on a second monitor. Participants can collaborate in real time, create an agenda, take notes, and add tasks. When tasks are assigned in the meeting, the user will receive an email notification and it will be synced with the Planner and To Do apps.
Meeting organizers can also add Collaborative notes to prepare for meetings by adding agendas or other materials in one place.
After the meeting Collaborative notes will remain accessible for all participants on the Teams calendar meeting details page. These can be copied easily out of the meeting and into chats, group chats, emails, and other documents. This makes prepping and follow-up even more seamless.
Collaborative Notes for Teams will roll out starting in May 2023.
Any questions or feedback? As always, feel free to reach out to our team at info@wecarecomputers.com.
February 15, 2023

Multi-Factor Authentication (MFA)
Since the beginning of the COVID pandemic there have been increasing numbers of remote workers resulting in more work occurring in the digital world. Hackers capitalize on this with increased cyberattacks.
Strong multi-factor authentication (MFA) is one of best options to prevent hackers from getting past the typical security systems in place. MFA provides an additional verification step to the process of logging on, preventing hackers with valid credentials from signing on. And while a hardware physical security key may be the best protection, other options are available at no additional cost. Here are options for configuring MFA:
* Use a hardware authentication device. A physical security key, designed to provide cryptographic proof of legitimate user interaction, is the most secure form of MFA system on the market.
* Use authenticator apps on phone. With an app users can securely authenticate multiple applications and websites by using just one set of credentials. Authenticator apps can supply a one-time login code after the application or website is registered on that app. Google, Microsoft, Authy and LastPass are among the companies that now have authenticator apps in place.
* Require a One-Time Password. A one-time password (OTP) allows users to authenticate a password sent to a registered email address. The OTP’s must be used within a short time frame or they become invalid. Since not all websites support email OTP, text messages or phone calls are often used too.
For any business with the remote workers cybersecurity is an evolving process that needs to be evaluated on a regular basis and upgraded in this ever-changing digital landscape. The information above should provide a good starting point in planning any cybersecurity upgrades.
Any questions or feedback? As always, feel free to reach out to our team at info@wecarecomputers.com
February 14, 2023

Bitlocker
With increasing threats of security breaches and sophisticated cyberattacks it has never been more important to protect company data from theft or exposure.
BitLocker is available as a convenient and secure solution for internal computer drives. As a data protection feature BitLocker encrypts drives and all user data, making data recovery impossible without the provided recovery key. Keeping the recovery key in a safe place is vital to recover data from the computer when depreciated or in the case of unexpected malfunction. Recovery keys are available for print out from the user’s Microsoft account, or from Windows settings on the computer.
Bitlocker To Go provides the same protection on external drives or flash drives. As with BitLocker, BitLocker To Go encrypted drives can be opened by using a recovery key on another computer. However, instead of a long string of characters to memorize on the go a password will be set to unlock the drive. This would allow anyone to encrypt their flash drives or removable drives to prevent data from being stolen. Additionally the drives would need to be wiped of data before they could be repurposed, securing the data from any theft or exposure.
For instructions on how to encrypt an external drive or flash drive, follow this link: https://tinyurl.com/bitlocker-to-go-instructions
Any questions or feedback? As always, feel free to reach out to our team at info@wecarecomputers.com
August 19, 2022

Windows 11 Update
Windows 11 was released in October 2021 to mass excitement and some measure of reservation due to concerns of compatibility with systems in use. While many users have adopted the new operating system with no issue, other users experienced technical difficulties and often opted to revert to Windows 10. The good news is that Windows 11 has announced an update coming out in September 2022 that will include several improvements.
App Folders for the Start Menu
Previously users could not create folders for their pinned apps, meaning each app would need to be pinned in its own allotted space, quickly clogging up the Start Menu. App folders will help to tidy up the space.
Live Captions
Ideal for those who are deaf, hard-of-hearing, or anyone that uses captions regularly, the Live Captions accessibility feature will allow for greater ease of use and could be invaluable for improved communication between users.
Task Manager
Although task manager has been in use in Windows for a long time, it will see a overhaul with this update featuring a new dark mode and better layout that includes a new command bar and efficiency mode to limit apps from consuming resources. For any users familiar with how Google Chrome can take up a large amount of RAM resources, this efficiency mode is a welcome addition to Windows 11.
With the additional changes coming to Windows 11 users can expect an overall improvement to the operating system.
August 18, 2022

Smart Pen Recommendations
While notetaking by hand is considered old-school in today’s technology-driven world it is well known that physically writing notes, reminders, or appointments helps us to remember much better than typed notes. Instead of using traditional pen and paper there are smart pens, notebooks, and tablets designed to save handwritten notes as digital files.
Digital notetaking options are highly recommended for users looking to take meeting minutes during staff meetings, quickly jotting down contact information from a phone call, or when traveling light between appointments. Just make sure the pen is on, regularly charged, and to transfer the notes to a computer before storage runs low.
This feat is accomplished using an infrared camera near the pen’s tip, tracking a user’s writing strokes when writing on the provided notebook The tracking data is plotted on a grid, displaying the notes as written. From there, the notes are transferred using Bluetooth or USB connection to a computer as PDFs, images, or Word and Google Docs.
Top rated smart pens for purchase include:
Neo Smartpen M1+ – The thinnest and lightest of the tested pens, it has the same feel of a standard pen making it intuitive to use. The Neo Studio app is also easy to navigate and allows for searching and editing the font for color of the notes.
Rocketbook Core – Reusable notebook with Pilot Frixton Pen, capable of taking notes, scanning photos, and erasing with a damp microfiber cloth. The Rocketbook app is also designed to keep everything organized, and send to Google Drive, Evernote, OneNote, and more.
Iskn Repaper Graphic Tablet – Enjoyable for taking notes or easily digitizing artwork drawn, Repaper uses a tablet and magnetized rings to immediately digitize notes while working. The Repaper Studio app will also show work done in real time or create shareable time-lapse videos for demonstrations or presentations.
There are many other models and options available, making this a highly customizable and versatile tool in our work lives.
May 3, 2022
Ad Blockers
We all know the annoyance of an auto-playing video ad or a popup that obstructs your entire view with only a microscopic X in the corner to close it out. What you may not know is that these ads can also cause issues well beyond the few seconds they repeatedly take out of your day. They can also be injected with malware and viruses that can wreak havoc on your machine.
A great way to protect yourself from malicious software is to install ad blocking software. There are many options available but we recommend AD Blocker and UBlock Origin. These applications, which often come in the form of a browser extension within your favorite web browser, are easily installed by visiting the links below and following the instructions on the page.
One thing to be aware of after installing these applications is that some websites will block access when using an ad blocker because they rely on the revenue from these ads to run the site. If you encounter this, they can be turned off by clicking the browser extension and enabling ads for the site.
Please contact our offices if you would like assistance installing ad blocking software.
May 2, 2022
Office 2013 Support Ending
We would like to inform you that Microsoft is ending support of Microsoft Office 2013. This means that they will no longer be releasing any security updates for the software which can cause greater vulnerability to malicious entities. If you are unsure of which version of Office you are using, please follow the instructions in the link below.
We recommend upgrading to Microsoft 365 subscription-based services which will allow installation on up to 5 computers and can be combined with the most robust email platform in the industry. Please contact our office if you would like to discuss upgrading or migrating to Microsoft 365.
December 17, 2021
Log4Shell Vulnerability
As the year comes to a close yet another major software vulnerability has made the news. This time it is the Log4Shell loophole that affects java-based software allowing attackers to penetrate the defenses of unpatched machines.
We have been following the developments of this vulnerability and have already pushed out mitigation techniques to subscribers of our managed services using several pieces of software we use to protect your computers every day.
We will be reaching out to any clients that need to have further steps taken. Please make sure that you turn on and restart any covered devices that have been off so they can receive these updates. We will continue to monitor any updates and implement any additional protections that become available.
December 12, 2021
How to be Cybersecurity Insurable
Over the past few years, we have gotten countless questions from clients about filling out Cybersecurity Insurance Questionnaires. Two of the most overlooked items on these forms are the utilization of employee training on safe technology usage (e.g. phishing, ransomware, phone scams, ….) and the implementation of multi-factor authentication. These are also two imperative pieces to your digital security. While knowing what to look for will help prevent information leaks, multi-factor authentication will ensure that even an attacker does get your password, they will still need access to your confirmed device before gaining access to your accounts.
At only $24.00/year/user ($2/month), We Care Computers offers a low-cost way of training yourself and your employees about up-to-date ways that hackers are trying to trick you. Test email campaigns, videos, games and more will help engage users to learn how to protect vital company data, as well as their own. This service is included in all of our User Support Plans (as well as unlimited remote support).
While educating users can help protect against many threats, attacks will get more advanced, and people will still make mistakes. Many sources report that multi-factor authentication will protect against 99% of password hacks which explains why it has been so commonly required by insurance companies. Thankfully many companies have implemented this feature into their security offerings and can be turned on in the security or privacy sections of that service’s settings page. We will be reaching out to our Microsoft 365 clients about turning this feature on for their users.
If you would like to sign up for our employee training program or want to know more about the multi-factor authentication settings of a particular service, please contact our office at info@wecarecomputers.com.
December 15, 2021
Email Blacklists and What to Do if You Are On One
Almost every email user can remember a time when they were expecting an email that just never showed up or they sent someone an email only to get no response. What many users may not know is that there are databases of spam offenders that can block them from sending or receiving emails without them even knowing.
While most non-custom domain emails (e.g. gmail.com, yahoo.com, comcast.com, ….) should take care of this themselves, custom domains may need to manually check themselves if they experience issues. Luckily there are sites that make this easy to do. Mxtoolbox.com has an easy interface to check many of the most common spam lists.
If you find yourself on a blacklist and would like assistance removing your domain from it, please contact our offices at info@wecarecomputers.com.
November 24, 2021
Keeping Your Device and Data Secure
Every week we get questions from our clients about securing their devices. Employees have become more mobile than ever, and this topic has gone from hot to scorching. Here is a basic list of steps you can take to make your device more secure during use and even some steps to help if you misplace it.
Require a password for all user accounts on the computer.
• While this may seem like a basic step, we find that many users still do not have a password on their devices. This simple practice will help block a large majority of people from getting into your computer. Without the ability to log in thieves will need to either boot to a different operating system or remove the drive from the computer to access data.
• Make sure the password is secure enough that no one can guess it, including people that actually know you. Many users have started using passphrases instead of passwords. By using a series of words the password will meet length requirements that make it hard to crack but will be easier to remember than a random string of characters.
o Secure Password Example: QSpf$CZK2E!i98RPJpuf
o Secure Passphrase Example: Perm-Overrate1-Treading
Use a screensaver that requires the user to input the above password to log back in.
• A screensaver will block passersby from viewing information on your screen when the computer is not in use for a predetermined amount of time and will then require the user to input the login credentials to regain access.
Secure your data with encryption.
• By using the built-in Windows feature “BitLocker,” users can secure their data from thieves capable of removing the drive or using an alternate access method. Decryption requires the user to use a recovery key that is created during the initial encryption process. It is important to save this key in a safe place like a password management tool.
Back up your data.
• In the result of your device being stolen or your data becoming otherwise inaccessible, the most important thing is being able to recover that data and the only way to do that is to have performed recent backups PRIOR TO THE LOSS OF DATA. We cannot emphasize enough how important it is to have backups of your data ahead of disaster. We recommend having at least a 3-point backup system in place. This includes your actively used data, a local hard drive backup, and a cloud backup. This way if any two of these backups fail there is still a copy to recover from. Just like insurance, it seems like a waste until you need it.
Update your software and protect your PC with antivirus.
• One of the first steps of staying safe in the digital world is to make sure you are running up-to-date software and have some sort of anti-malware and anti-virus software on your device. Updates help make sure that important vulnerabilities are closed as quickly as possible while security software will help keep an eye on what your computer is doing in the background to help prevent issues you may not even notice going on.
Additional physical protection for your mobile devices.
• Privacy screens will help prevent those trying to snoop over your shoulder from being able to view the screen at an angle.
• Webcam covers will help prevent malicious software from your camera being used to spy on you.
• Cable locks will help secure a mobile device to the table or another physical item to help prevent someone from walking off with it.
• GPS tracking will help locate a device if it is lost or stolen. This feature is only available on certain make and model devices.
Utilize remote wipe features from We Care Computers Managed Services.
• If your device is stolen and gets connected to the internet, our agents can attempt to send a command to remotely wipe the information from the device helping prevent the thief from gaining access.
Use a VPN.
• Using a VPN will encrypt the information being sent and received from the device while on a public Wi-Fi network. Some VPN services track the users so make sure to review privacy policies.
October 27, 2021
Changing of the Guard – The Birth of Windows 11
As many of you may have seen Microsoft has recently released Windows 11. This is the newest iteration of Microsoft Windows and will replace Windows 10. As with all major operating system upgrades, we make the general recommendation to hold off on upgrading from your current version for at least a few months until the incoming version has been fully tested by the general community. This will help ensure that bugs are fixed before relying on it for your daily computer usage. Microsoft will continue supporting Windows 10 until 2025.
There are a number of notable features and changes coming to Windows 11:
- A more Apple macOS aesthetic with lighter coloring and a start menu and taskbar moved to the center of the screen instead of the previously left aligned one.
- Microsoft Teams is getting further integration into the Windows environment with enhanced notification windows.
- Increased virtual desktop support allowing users to switch between personal, work, school, or any other task they would like to separate. This feature has become increasingly important as users work from home and do screen sharing during meetings.
- Better transition when plugging or unplugging a laptop to or from a docking station that aims to help keep your current windows right where they are.
- A wider availability of widgets, similar to those found on Android and iOS, allowing the user to have easy access to information and applications right on the desktop with live updated data.
- Android app functionality from the Amazon Appstore allowing users to use many of the apps they currently have on their mobile devices
As with all new major Windows updates, rollouts will be staggered depending on the specifications of the machine and other factors. Some users may have already seen the update prompts while others may have to wait until mid-2022. You can see if your computer is queued for upgrade by opening the Start Menu and typing “Check for Updates.” In this window you will see a notification if are either eligible for the upgrade or if your system is not compatible.
Requirements of Windows 11:
- Compatible 64-bit, two or more core processor rated at 1 Ghz or faster
- 4 Gb of RAM
- 64 Gb or more of storage
- Internet connection for activation
- UEFI and Secure Boot capable BIOS
- Trusted Platform Module 2.0 capability
- DirectX 12 or later graphics card
More details from Microsoft can be found here.
Some of those might be gibberish to you, but Windows 11 has a semi-typical set of requirements needed to run the software. The processor may limit some users with older machines from installing without the use of a workaround. The list of compatible processors only includes processors found in computers that are about 2-3 years old or newer. You can find the list here by clicking on either AMD, Intel, or Qualcomm in the Windows 11 row of the first table. Luckily there is a workaround involving using the Windows 10 and Windows 11 installers together.
If you are going to upgrade to Windows 11 please ensure you have done the following to prepare BEFORE upgrading:
1. Ensure compatibility with Windows 11.
2. Properly perform a full backup including the operating system, files, and applications.
3. Confirm access to all crucial files in case there is a failure of the upgrade or drive.
4. Make note of all important product keys in case of activation issues.
5. If updating a laptop, fully charge the battery and plug in the power adapter.
As always we are here to support you and are available to assist with the upgrade if needed. Please contact our office if you need assistance.
March 12, 2021
Microsoft Exchange Vulnerabilities
As many of you may have read, there have been some major vulnerabilities found in the Microsoft Exchange on-premises email platform. This platform is used by thousands of companies all over the world to host the email that they rely on each day.
We have not released any information about this vulnerability because almost all of our clients have been migrated from on-premises Exchange to Office 365, which does not have the same vulnerability. We have already reached out to all clients that are still using on-premises Exchange hosted systems and installed the necessary security patches.
We will be releasing some additional email security offerings in the next month to provide increased spam filtering, phishing protection, backup and increased security for the email that we all live and die by each day.
Look out for mailings on these exciting new offerings.
If you are interested in migrating your existing email platform to Microsoft Office 365, we provide full setup and data migration to bring you the benefits of shareable contacts, calendars, tasks, folders and much more with full synchronization across all of your devices for an affordable cost.
There is a reason this is only email solution that we recommend. We rely on it ourselves every day to provide you with the high level of customer support you expect.
March 11, 2021
LastPass Changes
Beginning March 16th, 2021, LastPass will require all users that use more than one type of device (e.g. desktop, mobile or web browser) to have a paid account. This will cause some users to look for a new password management tool.
Luckily there are alternatives out there that provide the same purpose as LastPass. One popular choice, BitWarden, provides free access to its core services in the same way that LastPass did but has the added benefit of being open-source.
For the non-techy, what that means is that the backend code for the program is openly available for review. While you may initially think that this is not a safe way of operating, open-source software is widely considered to be more secure than closed source software. The reason for this is that the code can be highly scrutinized for bugs and vulnerabilities before it is released to the public.
There are a number of other alternatives available such as Keeper, DashLane, 1Password and many others. Most offer similar functionality while some excel at certain aspects.
Fortunately, the process to export your passwords, notes and other tidbits out LastPass is easy to complete. After logging into the LastPass Vault, simply click Advanced Options in the bottom left-hand corner of the page. Then click Export and enter your master password to download a CSV file that can be uploaded into most common password managers.
If you need assistance making the swap or have questions on getting started, please call the office at 860-836-4191 or info@wecarecomputers.com.
January 27, 2021

Cleaning Up Your Inbox
It is no secret that emails tend to stack up more than chips in a can of Pringles. An inbox full of old emails can quickly lead to lost communication and overlooked tasks that eventually lead to missed opportunities. It is vitally important to stay on top of your inbox as it comes in as even a single day of avoidance can lead to extra work. Here are some tips on maintaining a clean inbox:
Note: Some of these may be dependent on your email host and method of access. (Indicated by an *)
- Decide on a folder structure and stick with it. Create folders for each common contact or subject so that you can easily organize.
- Create automatic sorting rules*. Doing so will automatically put new emails from p articular senders, containing certain subject lines, or meeting other criteria into a selected folder without user interaction. More info can be found here: Microsoft Outlook Rules.
- Unsubscribe to unused advertisements. Actively unsubscribing to any unused/unread emails will reduce clutter in your inbox. Sorting the remaining ones into folders with rules will help clean up the rest.
- Once you are done with an email move it to a secondary archive folder or delete it entirely. By creating a subfolder below each of your main folders (e.g. “Inbox” & “Inbox Old”, “Co-Worker #1” & Co-Worker #1 Old”, “Coupons” & “Coupons Old”, ……), you effectively create individually clean inboxes for all your main correspondents and topics. Rules would automatically send emails from a contact to their folder and once that email chain is completed, it can be moved to the “Old” folder for archiving if needed.
- Not everything needs to be saved. While it is better to err on the side of caution some things just do not need to be kept. One-time use codes, temporary passwords, spam emails and the like can all be deleted.
While these tips can reduce the amount of clutter and lead toward the Zen of an empty inbox, many users may not be aware of some of the basic and advanced features that come from using Microsoft Outlook to access emails. The following Cheat Sheet from Microsoft can provide some insight on these features.
Microsoft Cheat Sheet Outlook Mail for Windows
If you need more advice on taming your inbox, reducing spam, or training yourself or your staff on phishing and other online threats contact our office at 860-836-4191 or info@wecarecomputers.com
December 22, 2020
GogoGadget GoNetspeed
Over the past year we have promoted a new fiber-optic internet provider that has been offering a competitive internet service to West Hartford, New Haven, Wethersfield and other select towns in Connecticut, New York and Pennsylvania. GoNetspeed has recently announced that they will be expanding to new markets including Southington, Rocky Hill, Hamden, Bridgeport, Fairfield and more.
GoNetSpeed boasts many attractive features including:
- Residential and Business services
- Lifetime price guarantee
- All-in-pricing and no extra fees or taxes
- 24/7 support
- No contracts
- No modem rental costs
- Symmetrical download and upload speeds
GoNetSpeed does not offer TV or phone service and you will need to supply your own router at the time of the install. While there is a cost to acquiring this device, it will be quickly recouped by the lack of rental fees.
We can help get you connected with alternative TV or phone services and help with the selection and setup of a router for the install.
Please check their site for availability and contact our offices at 860-836-4191 or info@wecarecomputers.com to discuss any other questions you may have.
Remember to put We Care Computers into the referral box when signing up so they know we are there to assist you.
December 18, 2020
The Last Flicker for Adobe Flash Player
December 31st, 2020 ends not only what has been one of the most interesting years in recent history but also the end of a long-time accessory to internet mischief, Adobe Flash Player. Flash Player will officially be discontinued as of 12/31/2020. For the last 24 years, Adobe Flash Player has allowed millions of users to play online games, music, mobile apps, e-greeting cards and many other uses throughout the internet world. It has allowed simple graphics to come to life to create Jib Jab videos, streaming of countless hours of YouTube comment and even let thousands of malicious entities into computers across the world.
That’s right. The same Adobe Flash Player that many users have grown to love when it works and loathe when it glitches has constantly been a hotspot of security vulnerabilities throughout the years. It has been a common source of malicious advertisements, games and that seem to be real but contain malicious code that infects your PC once you interact with the flash window.
This is one of the many reasons we preach the use of our We Care Computers Managed Service which provides automatic updating of software like Adobe Flash Player, Java, Chrome, Firefox and many other programs, including Microsoft Windows itself. This service will help reduce vulnerabilities on your system and provide peace of mind to your online interactions.
Over the next month you may see prompts to uninstall Adobe Flash Player. While this may be a real prompt, there are also fake prompts that attempt to lure you into clicking them to cause problems. If you are unsure, please send a screenshot of the prompt to info@wecarecomputers.com and we will provide more information.
October 14, 2020
Introducing a new Low Profile Desktop from We Care Computers
Introducing a new desktop computer option for our clients. This new desktop form factor is custom built to maximize desk space, minimize cable clutter, and provide you with a complete setup for all your computing needs. It even comes with a complete 3 YEAR WARRANTY on all hardware to provide peace of mind that your investment will go the long haul.
The full setup includes a custom-built small form factor PC that fits in your hand but packs an i5 processor, 8gb of RAM and a 256gb solid state drive to give you the speed you need to get the job done. This unit is mounted and hidden behind a 23” monitor with built-in speakers and gives you the screen space to make life easy on your eyes. Tying this all together are a wireless keyboard and mouse from one of the most reliable names in the game, Logitech. The wireless input and shorter display cables eliminate the usual rat’s nest of cabling that most people have with a typical desktop setup.
We can also provide a more customized option with larger or dual monitor setup, webcam, or better performance options.
Pricing starts at just $1300.
July 22, 2020

Help Protect Your Data from Physical Device Theft
No matter how secure your passwords and accounts are device theft is always a major concern. Even if the users have everything locked up correctly the uneasy feeling of someone having your property is still there. To help mitigate that feeling we look to device tracking software. There are some protections built into mobile devices (e.g. Apple or Google’s Find My Device service) but what if that is not enough? What if you want to be alerted when a device is taken from the office?
For this we use the strong arm of Prey. This software allows tracking of devices and recording of evidence such as nearby WiFi networks or GPS (if available). It allows for automatic deletion of data, screenshots and snapshots of users and much more. For just the cost of a few dollars a month you can add some extra protection and peace of mind. Contact us for more information.
July 21, 2020

Manage Your Practice Using the Combination of Microsoft 365 and Matter365
We have recently partnered with an amazing Practice Management software for attorneys called Matter365. This platform sits right on top of Microsoft 365 and integrates fully with the cloud-based system to maintain a unified structure. Time spent is tracked within emails, documents and more with billing automatically exported to QuickBooks Online for invoicing. Unlike many other systems file names are left as they are, and tags are attached to each document to link them to a matter. This gives you full control and allows documents to still be usable outside of the management system.
Please reach out to our office if you would like to hear more about how Matter365 can improve productivity in your office or to schedule a demo.
May 20, 2020
PRESS RELEASE
West Hartford Information Technology Company is Collecting and Refurbishing Computer Equipment to Provide to Students Throughout Greater Hartford
Contact:
Avi Smith-Rapaport
860-836-4191
info@wecarecomputers.com
A West Hartford based technology company, We Care Computers, is collecting donated computer equipment, refurbishing it, and providing these devices to local students free of charge. They are working with school districts, municipalities, and nonprofit organizations to get the computers to the students who need them and have donated over 30 computers so far.
Avi Smith-Rapaport, owner of We Care Computers, had been hearing that there was a significant need for computing equipment among students that have been forced into remote learning over the past couple of months.
“I had been told by many people throughout the community that there was a shortage of computers for remote learners because of Covid-19.” Avi stated. “I got the idea for donating refurbished computers when I realized there was an inventory of available machines from organizations upgrading their equipment.”
Donations have come in from individuals, businesses, schools, and a few other organizations.
“We continue to post our need for used equipment through social media and our newsletter,” Avi went on to say. “We will continue to provide computer equipment as long as there is a need.”
Mr. Smith-Rapaport said that We Care Computers will gladly continue to take donated equipment as well as cash donations so they can expand the numbers of students that can receive computers.
They have set up a fund called WCC Students in Need:
https://www.gofundme.com/f/we-care-computers-students-in-need
For more information email Avi Smith-Rapaport at info@wecarecomputers.com or call 860-836-4191.
ABOUT WE CARE COMPUTERS
We Care Computers is a Managed Services Provider and full-service computer technology company providing onsite and remote computer support to businesses throughout Connecticut and western Massachusetts. For more information please see www.wecarecomputers.com.
May 19, 2020

We Care About More
Over the years we have strived to operate a business that not only cares about your IT needs but also about the overall well-being of our clients. We want to do everything we can to make sure that our clients are running at top capacity in all sectors of their business.
Throughout the last 16 years we have built relationships with hundreds of businesses and thousands of individuals that offer a wide variety of business services. By using the connections we have made we have been able to save thousands of dollars on the services we depend on while continuously streamlining operations.
We want to take a moment to touch on some of the areas where we have made changes that have improved our business in hopes that they can also improve yours.
Business Management Software
We now use a PSA (professional services automation) software called AutoTask. This software allows us to schedule our specialists, automatically export labor hours and parts to QuickBooks for billing, keep client notes, track sales processes and maintain overall business management with ease. While AutoTask is an IT-focused product there are purpose-built applications for almost every industry imaginable. Whether you have no business management software or you have something that does not do what you want, we can help you look for options to help make your business easier to manage, maintain, and grow.
Phones and Internet
As you may have read in recent newsletters, we have made the swap to new VoIP Phone and Internet vendors and could not be happier. We have been able to save money while adding new features and capabilities. We are happy to discuss how changes like these can not only save your business money but save yourself ongoing headaches at the same time.
Credit Card Processing
This is a field that almost all businesses deal with and credit card fees can add substantially to the costs of getting paid. By shopping around and finding a vendor that works we have been able to reduce our credit card processing fees to more agreeable rates.
Employee Safety
With talks of businesses beginning to open back up in the month(s) to come, we have prepared our own offices by having a protective coating sprayed on all the touchpoints in the office. PermaSafe is an anti-microbial coating that has become popular in the auto industry and is designed to provide disinfection that lasts for years. It is non-corrosive, non-toxic and odor-free. It can even be sprayed over electronics and will ensure that your employees can return to the office confidently.
If you have any questions about these tools please contact us at info@wecarecomputers.com or call 860-836-4191.
May 5, 2020
Boost Your Ability to Work Remotely with Fiber Optic Internet
For years there has been a split monopoly of internet provider choices in Connecticut and many other places across the United States. Those lucky enough to have the option of more than two internet providers will know the reliability and cost savings that can come from having a little competition in the area.
A new fiber optic provider is now giving parts of Connecticut that same competition by expanding into towns such as West Hartford and New Haven. With new fiber optic lines being run every day the fast expansion in the area brings not only an increase in options but quality customer service along with it. One of the major issues that users have with other providers is that prices can spike to unexpected levels after an introductory period. GoNetSpeed offers a Lifetime Price Pledge guaranteeing that their price will never increase as long as customers remain in the GoNetSpeed territory.
In addition to the stellar customer service features (such as the above pledge) fiber optic internet also provides symmetrical internet speeds. While this may seem like technical jargon to some people this can prove to be extremely valuable when working remotely.
When a user is in the office, uploading files to a centralized server is done locally and only has the limits of the internal network. When users work remotely the files need to be sent through the internet to arrive back at that same location. When this happens the upload speed of the user’s internet plays a huge part. Other providers offer non-symmetrical speeds and focus advertisements on the higher download speed. Many times there can be up to a ten-fold difference in the two speeds with packages such as 150Mbds download and only 15Mbps upload. This means sending a file BACK to a location can take longer especially when dealing with large files such as videos. GoNetSpeed’s symmetrical speeds ensure those files can be received AND sent at the same speeds.
If you would like to find out if your business or residence is in the GoNetSpeed service area, please go to https://GoNetSpeed.com and click “Check Availability” in the top right hand corner. Then input your address to see if you are in a current service area. Whether or not GoNetSpeed services your area it is worth it to put in a request as this helps them decide where they will be expanding to next. They begin looking at expanding to a new area once they reach a 10% request rate.
** Don’t forget to put We Care Computers as the referrer and in the notes so that we can assist with any questions you may have during the sign-up and setup.
If you have any questions, please reach out to us at info@wecarecomputers.com or call 860-836-4191.
April 28, 2020
Video Conferencing: Zooming Past Security Checks
As the world continues its trend of doing everything we can to work remotely, technologies that specialize in this ability have come to the forefront of news. Zoom has been one of the fastest growing video conferencing providers in the space but recent concerns of their security methods or lack of have come to light, not the least of which is a recently discovered cache of account password being released, for free, on the dark web.
Over half a million accounts have been found for sale for tenths of a penny or given away for free with information such as email addresses, Zoom account passwords and meeting links. These passwords were found using a method called credential stuffing, which is basically using a previously released credential set for another account, furthering the importance of not re-using passwords across multiple sites. While these accounts do not mean that Zoom themselves got hacked, it is just one more example of Zoom making the news over security concerns.
Recently a number of companies and government organizations have blocked access to non-specialized Zoom platforms and told their employees they are no longer allowed to use them on company property or for company purposes.
Just a few names on that list are:
- S. Department of Defense
- Taiwanese Government Agencies
- Google (Note: Google has their own business-class video conferencing platform)
Many of the concerns can be mitigated by using different levels of the Zoom products beyond the base $16/month membership or using features such as password protected rooms but other issues such as their encryption methods and China-based R&D teams lie at the root of the company itself.
The enormous amount of need for remote communication that is now needed have brought many of these issues to light as companies begin to more intensely vet the products they use in day-to-day business life.
While this is not meant to completely discount Zoom as a service, it is important to realize the limitations of the products we use each day. Other free alternatives such as Microsoft Teams and the open source Jitsi.org, can offer many of the same features while providing some additional advantages in security.
If you would like to discuss any of these other options or would like assistance in setting up secure Zoom meetings, please reach out to us at info@wecarecomputers.com or call 860-836-4191.
April 21, 2020

Microsoft Teams: A Key Tool in Communication
As we continue to quarantine ourselves it is important to stay socially interactive while remaining socially distant. One of the tools we use to do this is Microsoft Teams. Teams is part of the Office 365 Suite but has been released as a free product for businesses and schools to allow for robust communication during these times. While Zoom has been under the watchful eye of security teams as of late, Microsoft Teams allows for a reliable and secure way to communicate with your staff through text, audio or video chats, screen shares, file sharing and more.
Microsoft Teams has become an indispensable product for us in our business lives and we utilize it on all our devices to communicate.
Here are just a few reasons why:
- Conversation history is kept within the program, as well as within Outlook if you use Office 365 for email hosting.
- Simple integration with Outlook allows for Teams meeting creation with the click of a button – calendar access without needing to leave the Teams app.
- Every Office 365 service, including Teams, follow compliancy rules for HIPPA, SOC2, ISO 27001 and EU Model Clauses.
If you would like to see how Microsoft Teams work take a look at Microsoft’s interactive demo at https://teamsdemo.office.com and find additional online training for Microsoft products at https://support.office.com\en-us\office-training-center.
As always we are here to assist with getting you and your staff on the road to boosting your communication abilities with Microsoft Teams or with any other Microsoft questions you may have.
April 17, 2020
Not Selling in the Coronavirus environment: Maybe the best questions you can ask your customers
March 24, 2020

Working Remotely During These Times
As the news unfolds more each day and new precautions are taken to reduce the further spread of the Covid-19 virus, businesses will need new ways to survive and we will all need to help each other to help ourselves. While many businesses may have no way of operating during these times, new technologies can assist with reducing the impact that these precautions make and allow for at least some functionality.
In order to try to assist our clients and the community in maintaining some functionality of their businesses, we want to provide a breakdown of the tools we ourselves use to work remotely.
Email
When physical contact is brought to a minimum, digital contact becomes even more important and email is often at the forefront of that contact. There are many ways to host email in the digital age and each has their own advantages and disadvantages. By utilizing a reliable host like Microsoft’s Office 365 platform, we can ensure that there are resources put forth to maintain email flow during moments of high server stress. In addition to the reliability of cloud hosting, it allows for reliance to be taken off in-house server resources so that they may be shut down during times of power outages or inactivity. Migration to Office 365 can sometimes even reduce monthly costs below other third-party hosts.
File Access
While each organization is different and may have their own needs for business operation, one of the most basic needs is the ability to access the files and documents that make up day-to-day operations. The emergence of cloud file hosting has brought a new era of always ready file access. Business class hosts like our Egnyte offering allow for access from any device with an internet connection and the ability to cache files for offline use should internet not be immediately available. Setup of Egnyte can be done remotely and installation of device apps is a breeze. Once files are in the cloud, updates to these files are made immediately available for all members of your organization, wherever they may be working.
Phones
Now that many businesses have made the swap from traditional landline phones to VoIP systems that work over the internet, phone systems are no longer tied to the office building where they were installed. A cloud-hosted VoIP provider like our partner, RingCentral, allows users to disconnect their phones in the office and take them home to continue communications as they would in the office. Phone transfers, conference calls and more can all take place from the comfort of our homes without the need for expensive hardware to handle the calls. Onboarding with RingCentral can be done in less than 2 weeks, including porting over your existing numbers.
Cloud Hosted Applications
When deciding on the mission-critical applications that run your business, there are often cloud hosted options or alternatives that can be used to maintain a level of functionality that was not possible 10 years ago. Cloud hosted options will provide a greater level of mobility and help allow your business to maintain during times when in-office usage is not possible. We can assist with deciding between the numerous options and help you prepare for disaster in the best way possible.
VPN
Even when cloud-hosting options are not available, a VPN connection to your office will plug users into the internal resources they need to continue working. By utilizing a business-class firewall, such as a SonicWALL, these connections can be in place and ready when they are needed.
Additional tools
• Reliable internet – While a multitude of internet provider options is often not available to many users, choosing between providers and the plans they have to offer can be daunting but we recommend using a reliable cable or fiber optic internet connection whenever possible.
• Comfortable setup – Bringing home a laptop may be easy for many users, but sometimes working at that laptop is not as easy. By taking advantage of docking stations, wireless keyboards and mice, multiple monitors and other tools, users can make the switch between office and home effortlessly.
As we make our way through the problems at hand, we will need to band together to ensure that we remain healthy and happy. Many workers are afraid of what is to come and have a reasonable uncertainty about the weeks and months ahead. By supporting each other every day and making sure our family, friends, neighbors and community stand united in an effort to overcome and maintain we can be sure that we as a people will make it through these times stronger than before. Helping your community by buying gift cards to places such as local restaurants will help make sure that your favorite local businesses can stay afloat during these times.
We will be here to assist you with maintaining your business as much as we can reasonably do so over the coming weeks, months and beyond. If you would like more information on implementing any of these tools we are available during our regular office hours for remote support so please call 860-836-4191 or email us at info@wecarecomputers.com with any appointment requests.
Stay smart. Stay safe. Stay productive.
The We Care Computers Team
March 6, 2020
What Can You Do With the Power of Two Monitors
For some users having multiple monitors may be nothing new but for the uninitiated it can revolutionize the ability to multi-task. Being able to dedicate each monitor to a separate task while seamlessly moving between the two without the need to click through windows allows users to shave seconds of their workflow hundreds of times a day. Over the course of time these seconds can add up to hours of extra productivity for yourself and your staff.
Most users will find that they have one or more applications that they spend large amounts of time in during the workday. By placing these applications (e.g. email, company database, etc.) in their own dedicated space, the user can help build muscle memory that will make finding information effortlessly efficient.
You may be asking yourself, “what if I am already using multiple monitors?”
Well, we still have some helpful tips and suggestions for you to make the most out of your hardware.
- Make your space your own with a mount that will help position the monitors at just the right height and help reclaim your desktop space.

- Memorize keyboard shortcuts to perform common tasks even faster.
Keyboard Combination Action Secondary Action Win + Home Minimize all but the current window Win + M Minimize all windows Win + Up-arrow Maximize the current window Win + Down-arrow Minimize the current window (if not maximized) Restore the current window (if maximized) Win + Left-arrow Snap the current window to the left half of the screen Cycles the half-sized window to the left through additional screens Win + Right-arrow Snap the current window to the right half of the screen Cycles the half-sized window to the right through additional screens Win + Shift + Up-arrow Extends the current window to full vertical height leaving horizontal size Win + Shift + Down-arrow Restore the current window (if maximized) Minimize the window Win + Shift + Left-arrow Move the current window to the left screen Cycles through screens to the left Win + Shift + Right-arrow Move the current window to the left screen Cycles through screens to the right - Why stop at 2 monitors? Some computers can even use 3 or more monitors to allow for more screen space.
- Docking stations and upgraded video cards can add the capability of multiple monitors to laptops or desktops without multiple outputs.
- Ultra-wide screen monitors can provide the same functionality of multiple monitors without the space between monitors or need for multiple outputs and power connections.

It may take a few days to get used to the multiple monitors but once the break-in period is over the functionality can be indispensable. If you would like to maximize your multi-tasking please reach out to our offices to find out what you will need to get started.
November 27, 2019
Email Spam and Phishing

The best way to prevent phishing attacks is to know what to look for when suspicious emails arrive in your inbox. Here are some ease ways to help weed out phishing emails from the rest of your legitimate emails:
1. Double check the sender’s email.
It may appear to be from a known contact or company, but make sure to check that the email and domain match up. Example: John Smith (jsmith@notyourcompany.com). Many times phishers will change the display name to a name you may recognize to get you to follow the links or download a file. . If your contacts are receiving strange emails from you, make sure to check the actual email address to verify that it did or did not come from you.
2. Double check the link.
By moving your mouse over the link without clicking on it, the address that it directs to will be displayed. Try it on this link: http://www.wecarecomputers.com/
3. Just because it looks real does not mean it is.
Most phishing scams that are attempting to retrieve login information will copy the real login pages from common email sites in order to lull you into a sense of false comfort.
If you would like to test your ability to recognize phishing emails, take the Sonicwall Phishing IQ Test at the link below:
https://www.sonicwall.com/en-us/phishing-iq-test-landing
If you would like to additional training, please call (860-836-4191) or email (info@wecarecomputers.com) our office to discuss the options available for training on Phishing, Ransomware and more.
June 1, 2019
Windows 7: That’s All She Wrote
Are the 2020’s coming faster than you thought? It is certain that big things will happen in the next 10 years but before that happens we need to concern ourselves with what happens in the next 7 months. On January 14th, 2020, the Microsoft Windows 7 operating system will be put out to pasture and Microsoft will no longer provide support for it.
Microsoft will no longer release security vulnerabilities patches or update other important features that may affect reliability. This can leave serious security issues without these important updates.
In order to stay protected with a supported operating system, you will need to upgrade your computer to Windows 10.
To find out if which version of Windows operating system you have:
• Open the start menu by clicking the Windows icon in the bottom left hand corner of the screen.
• Type System Information in the Search box and then open the resulting item.
• Operating System version will be listed under OS Name
If you are running Windows 7 and would like to discuss upgrading to Windows 10, please call us at 860-836-4191.
May 31, 2019
Managed Services Update – New Features for Mac Users
We are excited to offer some new features for our Mac OS clients on Managed Services (compatible with Mac OS 10.11 and above). We will be activating a new antivirus in the coming month to swap compatible users over to BitDefender antivirus.
In addition to the new antivirus offering, the same great managed document backup solution we offer to our Windows clients is now available for our Mac OS clients (Mac OS 10.11 and above). For now, this is limited to office documents of specific file types (details below) but a full backup option is in the works and will be released in the future.
Document Protection – $5/month per computer
Automatic backup any office documents twice a day. These documents are held for 28 days providing 58 restoration points for a single price.
File types include: Word, Excel, PowerPoint, PDF, OpenOffice, TXT, Microsoft Works, WordPerfect.
May 30, 1019
Maintenance Schedule
Here is a suggested schedule for computer maintenance:
DAILY/WEEKLY
Update antivirus *
Perform virus scan *
Check for critical updates *
Reboot
(* Performed Automatically Under our Managed Services)
MONTHLY
Check event logs
Delete temp files
Check local backups
EVERY 3 MONTHS
Change passwords to email and domain login
EVERY 6 MONTHS
Check for third-party software, driver and BIOS updates
Remove old downloads and unused software
Employee Q&A
Secondary malware scan
Hard drive check and defrag
YEARLY
Physically clean device and perform cable management
Battery backup checks
Clean and reorganize file structure
Disaster recovery testing
Hardware audit
Group Policy review for domain users
Penetration testing for security vulnerabilities and phishing email testing
Change passwords to all logins
December 20, 2018
Microsoft Office 2019
Another 3 years has past, so it is time for a new version of Microsoft Office. Now that Microsoft has had a few months to work out some kinks, we are offering the new 2019 version of the Office software to our clients in need of a new install or upgrade. With some major changes in the core applications, here is what you are missing by running an older version:
1. Translations
New to Word, Excel and PowerPoint is the ability to translate words, phrases, and other text selections to another language with Microsoft Translator.
2. PowerPoint’s Big Additions
PowerPoint has become slicker than ever with the addition of slide morphing , zoom capabilities allowing you to flip to other slides without changing your current slide location, and the ability to use the Surface pen as a remote.
3. New Visual Effects
In Word, Excel and PowerPoint, users can now add Scalable Vector Graphics and even apply filters to those graphics. The new Inking feature brings the ability to draw on documents using a touchscreen or mouse. Office can then convert these drawings to moveable shapes.
4. LaTeX Equations
Word now gives the ability to create complex math equations using the LaTeX syntax.
5. And Much More…..
New Functions in Excel. New Charts and Data Types in Access. Simple click to link tasks in Project and easily view progress of those tasks. New Diagrams and Templates in Vizio.
If you are ready to dig into more of what the new Microsoft Office 2019 has to offer check out Microsoft’s website. You can also find helpful Microsoft tips, training and quick start guides here.
If you have any questions or would like to order Office 2019, please contact our offices at 860-836-4191.
November 19, 2018
Preparing for the Worst
Nobody wants to think about death but it is something we will all will have to face, along with our loved ones. It is important to be sure that your digital life is organized. Everything from credit card access, financial institutions, email, social media profiles and more should be organized so that your loved ones can properly close down any unneeded accounts. To make sure you are ready follow these quick tips:
1. Make an inventory of your current digital accounts.
• Financial Institutions
• Utilities (Electric, cable, etc.)
• Social Media Accounts
• Email Services
• Other various accounts
2. Make sure you are aware of the correct passwords and record them for easy access.
Set up a password management product such as KeePass, LastPass, Dashlane or 1Password to simplify this process. By keeping all of your information in a password manager, you will only need to provide a single password to your loved ones to access the rest of your accounts.
3. Make note of any accounts with 2 Factor Authentication
Using 2 Factor Authentication greatly increases security but will make it harder, if not impossible, for your loved ones to access your accounts when needed. Make sure to record the 2 Factor Authentication recovery codes provided during setup of this feature and store this along with the password information.
If you need assistance in setting up a password manager or have any questions on what we can do to prepare your digital assets, please contact our office at 860-836-4191.
November 13, 2018
Why Small Businesses Matter – We Care Computers
 HamletHub has published an article about We Care Computers. Read the article here.
HamletHub has published an article about We Care Computers. Read the article here.
October 24, 2018
Phishing – Educating your Staff

Our WCC Managed Services will mitigate the effects of malicious entities online, but the best prevention from phishing attacks comes from user education. By training your staff on what to look for, you can help avoid these threats altogether. Some of the biggest threats come from phishing emails that are infected with a malicious file or links to websites trying to get your passwords. Luckily there are some easy ways to help weed out phishing emails from the rest of your inbox.
1. Double check the sender’s email.
It may appear to be from a known contact or company, but make sure to check that the email and domain match up. Example: John Smith (jsmith@notyourcompany.com). Many times phishers will change the display name to a name you may recognize to get you to follow the links or download a file.
2. Double check the link.
By moving your mouse over the link without clicking on it, the address that it directs to will be displayed. Try it on this link: http://www.wecarecomputers.com/
3. Just because it looks real does not mean it is.
Most phishing scams that are attempting to retrieve login information will copy the real login pages from common email sites in order to lull you into a sense of false comfort.
If you would like to test your ability to recognize phishing emails, take the Sonicwall Phishing IQ Test at the link below:
https://www.sonicwall.com/en-us/phishing-iq-test-landing
If you would like additional training, please contact our office to discuss the options available for training on Phishing, Ransomware and more.
October 22, 2018
Comcast’s New Failover Internet Option

If you are a Comcast internet customer, a new service has been released to make sure you are always connected to the internet. By adding a 4G cellular hotspot connection and Comcast Cradlepoint router, your Comcast router will automatically cut over to a 4G connection if the main connection cuts out. While the service will be much slower than that of the traditional connection, it will ensure important functions such as email and credit card functionality will continue in the event of a power failure.
This service is available at a cost of only $29.95 a month and also includes an 8-hour battery backup.
If you are interested in adding this feature for your business or home, please contact our office and we will refer you to a Comcast representative.
August 10, 2018
You Have the Power…. Until You Don’t
When setting up a computer for the first time, some users unsuspectingly plug them directly into a wall outlet thinking this will be fine and not knowing the real truth.
Not all power outlets are created equal.
A computer plugged directly into the wall is susceptible to power surges from lightning, electrical line issues, blown fuses and more. These electrical surges can destroy computer components, including the hard drives that store your valuable data, leaving you with a hefty bill to recover from these disasters.
Power strips and surge protectors are not the same thing.
While many people use these terms synonymously, a power strip is essentially just a way of adding more physical outlets to a wall outlet. One side plugs into the wall and the other has multiple outlet in a strip. Unless the strip says surge protection somewhere on it, it is most likely not going to provide protection from a harmful electrical surge. The red power switch alone is also not an indicator of this feature.
Surge protectors are not good forever.
Once a surge protector has been tripped by an excess electrical current, that surge protector should be replaced. They can also wear out with time and should be replaced after about 3-5 years to be safe. After all, a $15 surge protector is a lot easier to replace than an entire computer or a decade worth of photos.
A battery backup is even better than a surge protector.
A surge protector will help prevent damage from excess electrical current but an abrupt stop to that same electrical current can also be damaging for your devices. A battery backup will ensure that your computer has a few extra minutes to prepare itself for this event and by utilizing the USB connection your computer will automatically shut itself off to prevent damage. These few minutes can also provide one last chance to save the documents you have been working before losing power.
It is important to use the proper accessories to prevent these issues from occurring. These tips will help you to get the right equipment for the job.
If you would like to ensure you are properly protected or purchase a battery backup for your systems please call us at 860-836-4191.
August 8, 2018
Why We Recommend Solid State (SSD) Drives

More Durable
Because there are no moving parts SSDs are generally more durable when compared to traditional hard disks.
Fast
They are super fast. If a computer has no malware and sufficient RAM the largest bottleneck for speed will be the hard disk! An SSD is about 100 times faster than a traditional hard disk and computers will boot up in less than a minute.
Go Green Save Energy
SSDs consume less power. For a laptop or table, you will be able to get more minutes out of your battery life.
Lightweight
For laptops, SSDs will reduce weight. An average SSD is 77 grams, while an average traditional hard disk is 752 grams.
Cool and Quiet
SSDs will run cooler, and make virtually no noise.
May 29, 2018
Time to Reboot your Routers

It was recently revealed that a group named the Sofacy Group has been able to infiltrate hundreds of thousands of routers in over 50 countries. Many major manufacturers such as Linkysys, Netgear and TP-Link have already been found to be compromised. A full list of devices has not been released but it is believed that a large number of manufacturers and models have been infected by the malware, called VPNFilter.
The Sofacy Group aka A.P.T. 28 and Fancy Bear, is believed to be under the direction of Russia’s military intelligence agency and is best known for being connected to the hacking of the Democratic National Committee prior to the 2016 Presidential election.
Effects of the VPNFilter malware include data surveillance, using your device to continue the spread to other devices, cutting off internet access and more.
The good news is that the FBI has already taken action to seize the domain used to communicate back to the originators in order to reduce further spreading.
Reducing the effects on your devices can be done by rebooting your router but, as always, the firmware should be kept current in order to provide the best protection. Additionally, any routers using default passwords should be changed to a more secure choice.
If you unfamiliar with how to reboot your router (which can be done by unplugging for 30 seconds) or how to upgrade your firmware we are happy to assist you in the process.
Confirmed list of infected devices: (this list does not include all affected devices)
• Linksys E1200
• Linksys E2500
• Linksys WRVS4400N
• Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, and 1072
• Netgear DGN2200
• Netgear R6400
• Netgear R7000
• Netgear R8000
• Netgear WNR1000
• Netgear WNR2000
• QNAP TS251
• QNAP TS439 Pro
• Other QNAP NAS devices running QTS software
• TP-Link R600VPN
May 25, 2018
Windows 10 Updates

It is time for another round of big Windows 10 updates to roll out. With the recent 1803 update, we have seen some issues with clients that use Avast or AVG antivirus programs. Several computers have come in not being able to completely boot up after the update was performed. We were able to get into the user profile to see that the update had completely botched the Windows installation, rendering it useless. There have been other reportable instances of this occurring with both Avast and AVG.
As with any large Windows update, it is recommended that a full backup of the computer be performed and any antivirus protection that may interfere with the update be turned off. It may also be necessary to uninstall the antivirus completely.
If you find yourself prompted with an update, make sure to follow the proper steps to ensure the installation goes smoothly or call us so that we can assist you with the update. If you are on Avast or AVG, this is a great time to consider our We Care Computers Managed Services with World-Class Bitdefender Antivirus.
Call us at 860-836-4191 for more information.
May 9, 2018
Scareware – What is it and how do you get rid of it?
What is it?
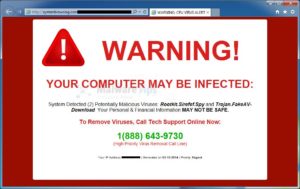
Scareware is malicious software that tricks computer users into visiting malware-infested websites. The reason it has this name is because it is designed to scare you and make you think there is something wrong with your computer. The good news is that this message is almost always just a persistent pop-up that stays in front of other windows.
How do I get rid of it?
The best way to get rid of these messages is to follow these steps:
Note: You will lose all unsaved work that had been done during your internet browsing session.
Windows
1. Hit the ctrl-alt-del buttons at the same time or right-click the time in the bottom right hand corner of the screen and click Task Manager in the menu that pops up.
2. In the window that opens, left-click the name of the web browser you are using. The most common choices are Google, Chrome, Firefox and Internet Explorer.
3. Click End Task.
4. Reopen the web browser and choose to not restore closed pages if the option is given.
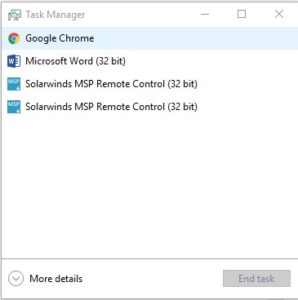
Mac
1. Hit the command-option-esc buttons at the same time or left-click the Apple menu in the top left-hand corner of the screen and click Force Quit in the dropdown menu.
2. In the window the opens, left-click the name of the web browser you are using. The most common choices are Google, Chrome, Firefox and Safari.
3. Click Force Quit.
4. Reopen the web browser and choose to not Restore closed pages if the option is given
Why?
These messages are most commonly received by clicking on a malicious ad or mistyping the name of a website (e.g. amazno.com, mircosoft.com, facebok.com).
The hope of those that put these messages there is that you will call the number in the warning. They will tell you that you have a serious problem with your computer and that they can help. They will request access to your computer by using a remote desktop application. Once in your computer they can copy files from your computer to access confidential information or use benign technical information to attempt to convince you to buy counterfeit software from them. There are many ways that they can make money from this scam but the important thing to remember is that there is a reason it is called SCAREWARE.
If you need help with any unwanted popup message, please call us at 860-836-4191.
February 22, 2018
Welcome to our new website! We are introducing a new exciting and modern design to our logo and website. Please send any comments/suggestions to info@wecarecomputers.com. Thank you for you continued support.
Unlimited Monthly Maintenance Plans
We Care Computers now offers an ALL INCLUSIVE/PLATINUM Monthly Maintenance Plan. With this package we will monitor your systems, back up your files, protect you from malicious web traffic, update your servers and much more.
The all-inclusive plan includes:
- Remote help desk support
- Onsite repairs – normal onsite repair for hardware malfunctions/minor repairs
- Server support – remote and onsite
- Switch and firewall management
- Remote monitoring/management of all workstations and servers:
- Remote monitoring
- Antivirus protection
- Web protection
- Patch management
- MOB – 500gb per server
- Monthly reports
- And Much More
Call us at 860-836-4191 for more information.